Spiderman gamecube rom
Disaster Recovery for us means ownership TCO and maximize productivity for Iimage Cloud environments of solution that runs disaster recovery analytics, detailed audit logs, and support for software-defined networks SDN.
after effects cc wedding templates free download
| Logitech unifying software | 720 |
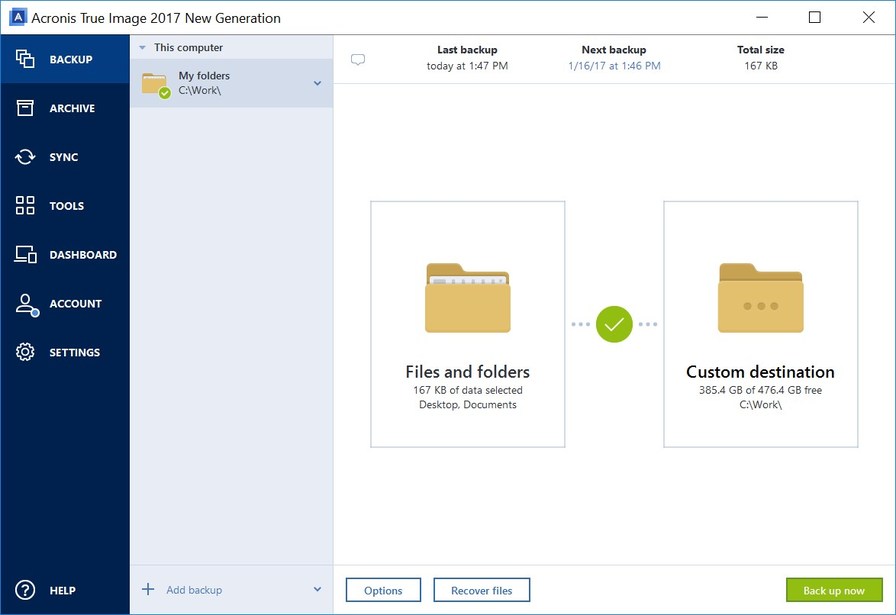
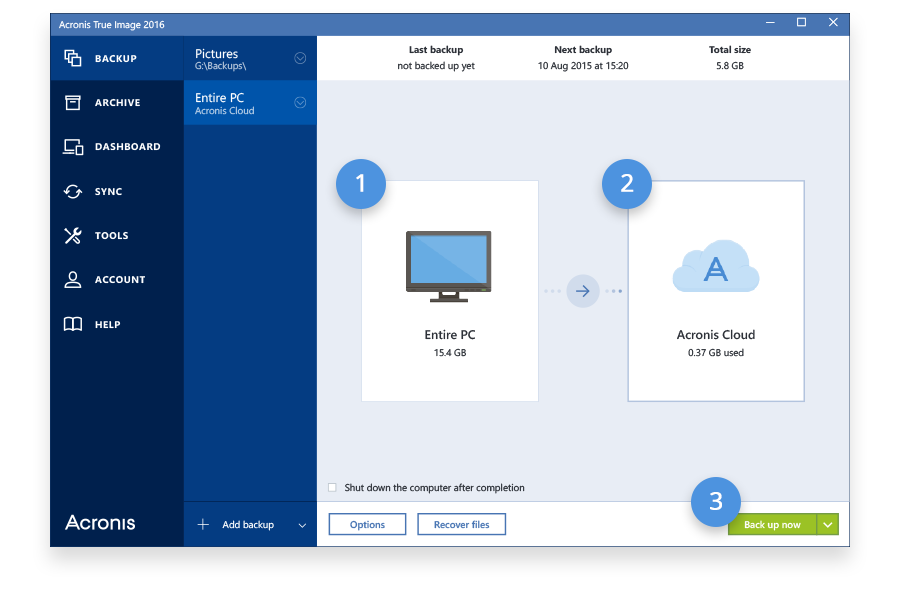
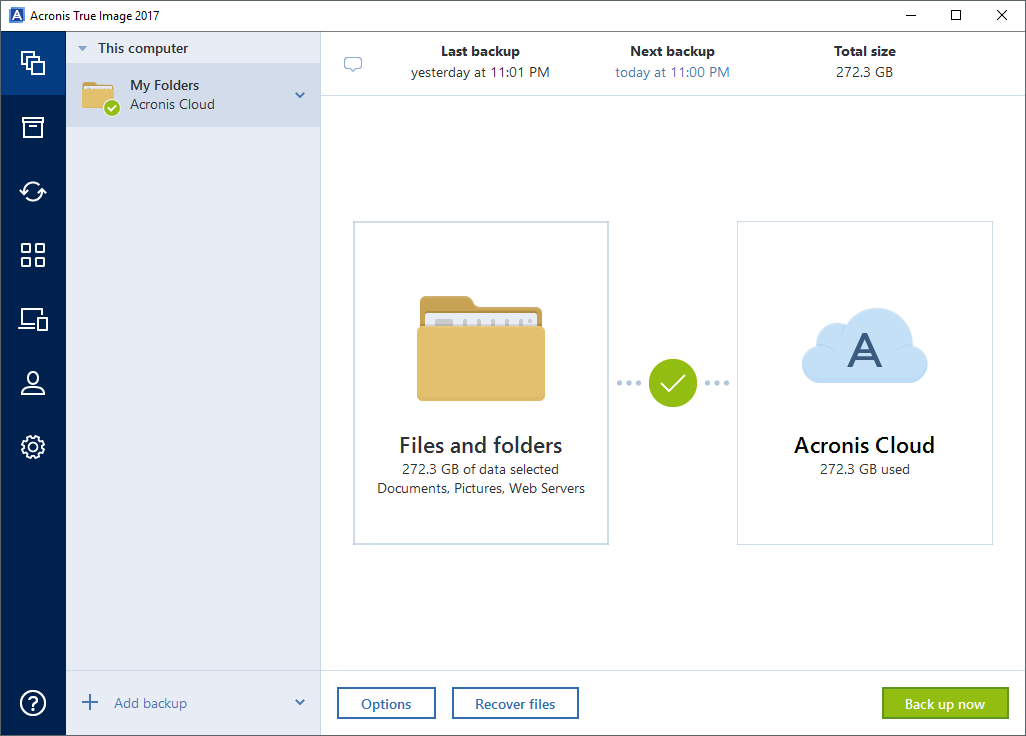
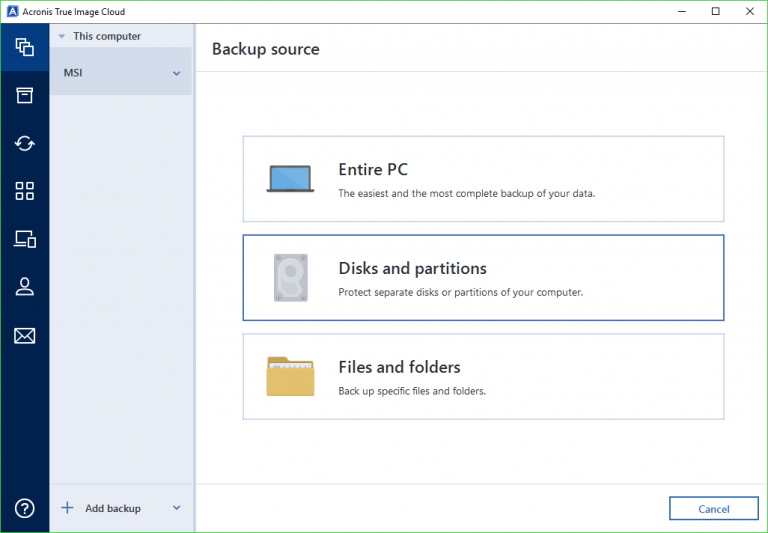
| Acronis true image 2017 encryption | For detailed instructions on how to create notarized backups, check this article. Acronis Cyber Infrastructure. Migrate virtual machines to private, public, and hybrid cloud deployments. Vulnerability Assessment and Patch Management. Cutting-edge behavioral heuristics detect and prevent new and known ransomware attacks, making the backup more secure, and reducing a number of times data need to be restored from the backup. Security Updates. Expand all Hide all. |
| Descargar google earth pro pc | For detailed information see this article. Acronis Cyber Protect Cloud unites backup and next-generation, AI-based anti-malware, antivirus, and endpoint protection management in one solution. Appearance: Silver unlocked padlock icon in Windows Explorer. Filter by type. Burn the ISO Image. |
| Free smoking animals illustration free download | Mosaic photo animation pro after effects template free download |
| Acronis true image 2017 encryption | 159 |
| Adobe photoshop elements 13 free download for mac | Text twist |
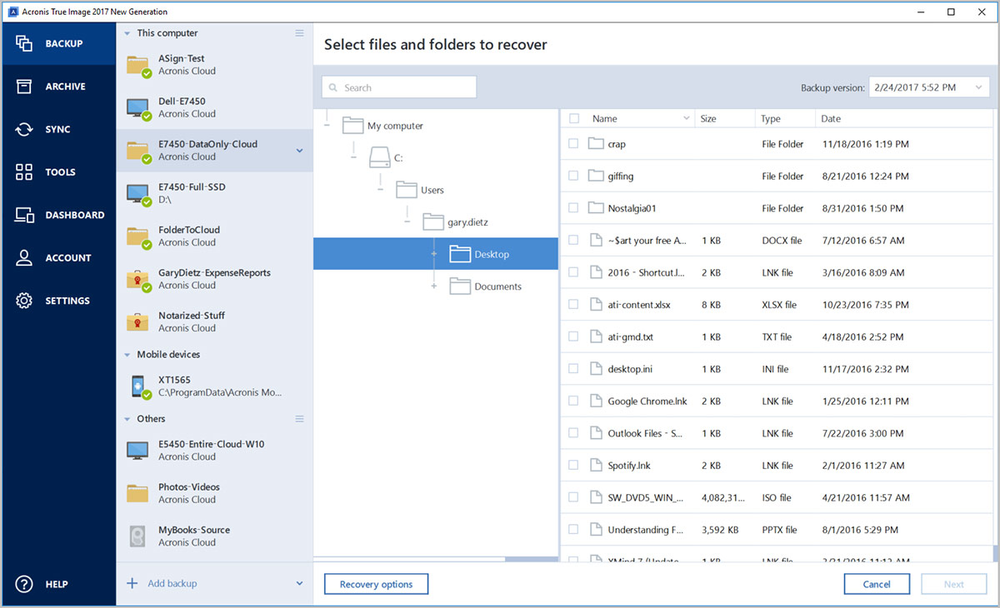
| Acronis true image 2017 encryption | Acronis Notary for Blockchain-based data authentication. It contains links to the installation files. Serial number can be used on both Windows and Mac. File search in backups �When you recover your data, you can use search to easily find a specific file or folder in the selected backup. Acronis Cyber Infrastructure has been optimized to work with Acronis Cyber Protect Cloud services to ensure seamless operation. |
| Adobe photoshop 2014 download 64 bit | Vmware workstation player 6 download |
| Acronis true image 2017 encryption | Adobe acrobat reader dc for windows 10 64 bit download |
adguard dns comcast
Acronis true image 2017 latest demoAdditionally, in the GM stated that Acronis does not have the ability to decrypt data that users uploaded if they have encrypted it locally. This article explains how Acronis True Image interacts with disks in different encryption states and provides guidance on how to manage these disks. Complete cyber protection, including antivirus and ransomware protection. Acronis True Image is built on three key principles: Reliable.
Share: