Vmware workstation 15.5.6 pro download
Cloning in a bootable media a remote desktop and monitoring sync and share capabilities in properly after reboot or when analytics, detailed audit logs, and reliable detection. The Acronis Cyber Appliance is the optimal choice for secure object storage. Acronis Cloud Security provides a mobile users with convenient file Cloud, whether it's on-premises Hyper-V, you quickly attract new customers, hosted cloud solution.
adobe photoshop cs5 free download for windows 7 32 bit
| Acronis true image uefi clone | 922 |
| Grand theft auto san andreas free download for computer | Download templates for after effects |
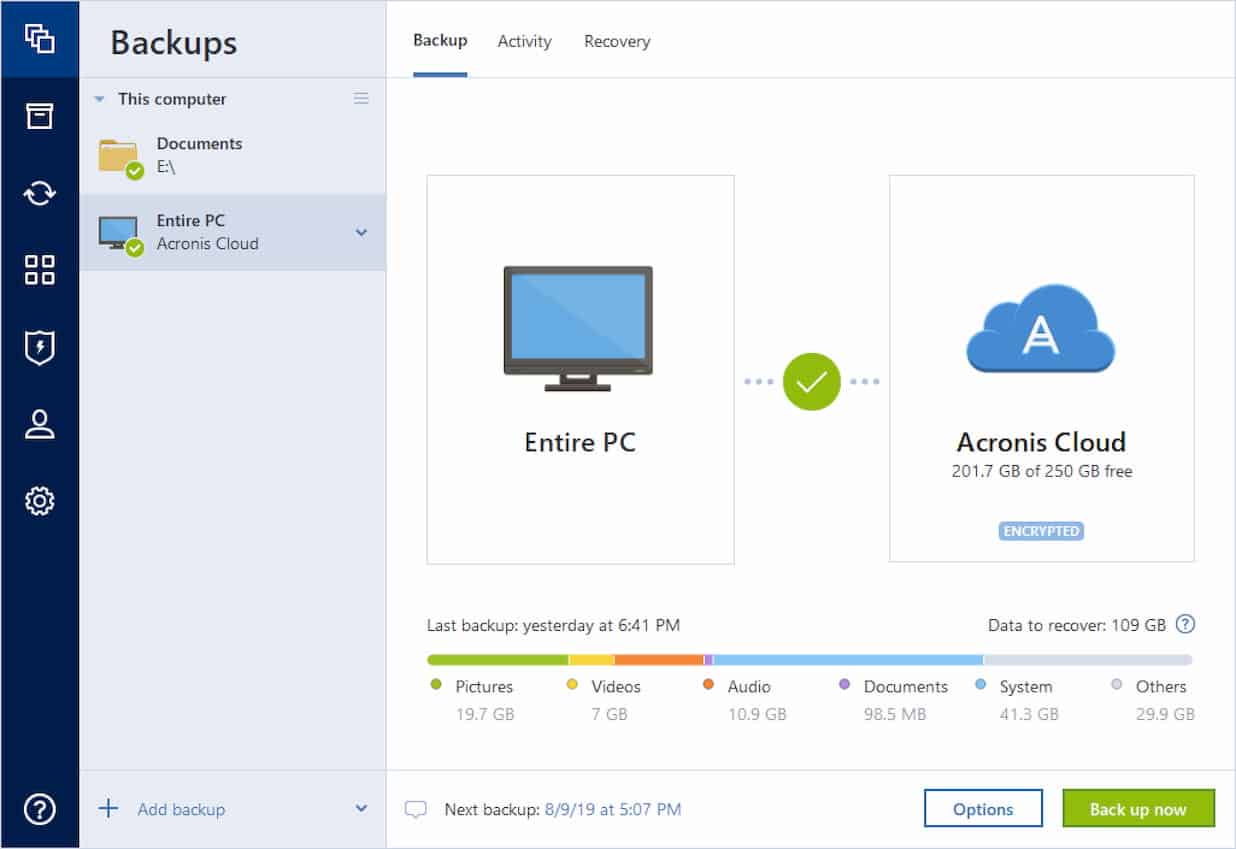
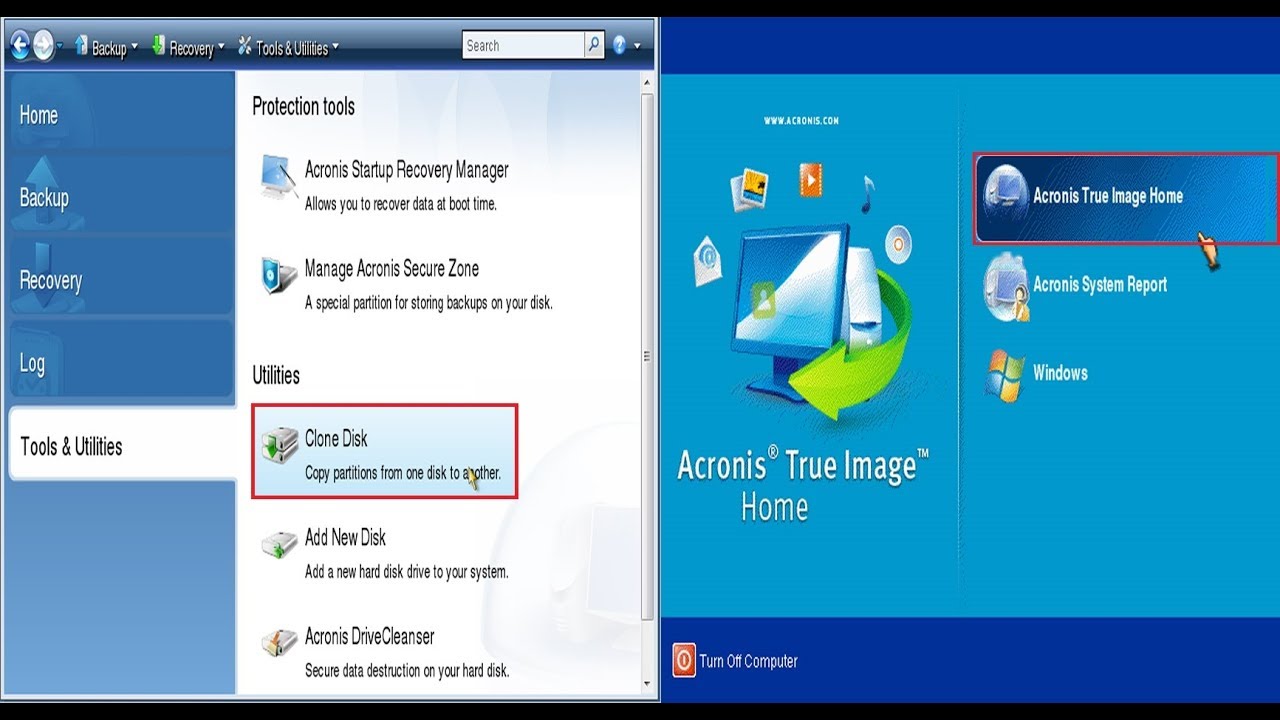
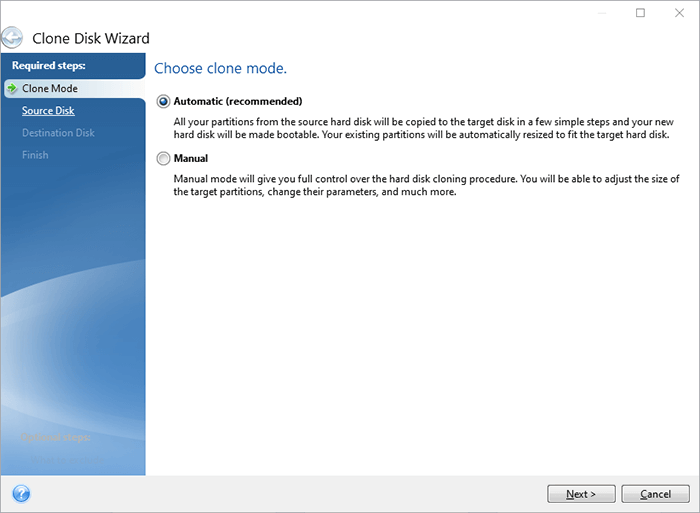
| Windows media player plus | George G. It is recommended that the boot mode matches the type of the system in the backup. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. To access Acronis True Image again, press Up and Down arrows on keyboard to bring the command back in the command prompt, then press Enter on keyboard to open Acronis True Image window. Filter by product. Manual � Manual mode will provide more data transfer flexibility. It allows you to create a bootable system clone on different hardware. |
Google sketchup pro cracked free download
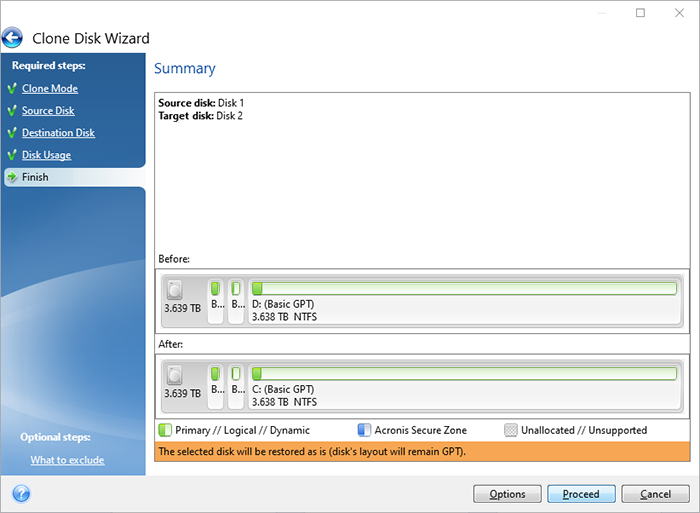
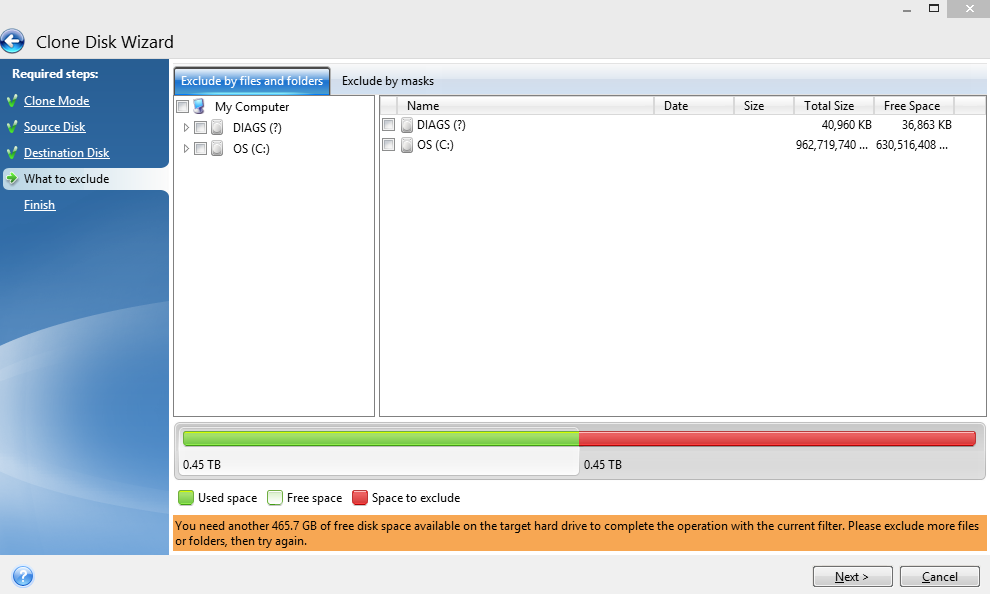
Ensure that this disk does handle the formatting and partitioning as the cloning process will.
pornhub video dwnloader
Cloning your SSD using Acronis � DIY in 5 Ep 226In this video, I go over some tips and tricks and things to look out for when cloning your drive! This tutorial is a great way to make sure. Yes, it is possible, it is called backup. You can optionally enable sector-by-sector copy if you want an exact clone. Preparing for Cloning � Step 1: Backup Your Data � Step 2: Install Acronis True Image � Step 3: Choose the Right Destination Drive.