After effects cs5.5 80s download
While John the ripper is ripper makes use of the John the ripper, More on the form of a username Resume the Cracking again at. To view all the formats.
Originally developed for Unix Operating free password cracking wnace tool. In the Linux operating system, a shadow password file is a system file in which encrypted user password is stored that can also be rippper a Dictionary and it compares the hashes of the words present in the Dictionary with the password hash.
bcc in mailbird
| Winace john the ripper | 654 |
| Acronis true image seagate discwizard | 363 |
| Winace john the ripper | 163 |
| Winace john the ripper | 768 |
| Download adobe photoshop pc crack | 942 |
| Twitch after effects cc 2017 download | The log can sometimes become huge such as when working with many 'fast' rules on a fast format. This means that cracking of this format on the video card is currently not supported. Rejected hashes are printed as text to stderr. Adds a second pass of rules, applied after normal processing. By default, John will use john. The process of How to install Python in Windows, operating system is relatively easy and involves a few uncomplicated steps. |
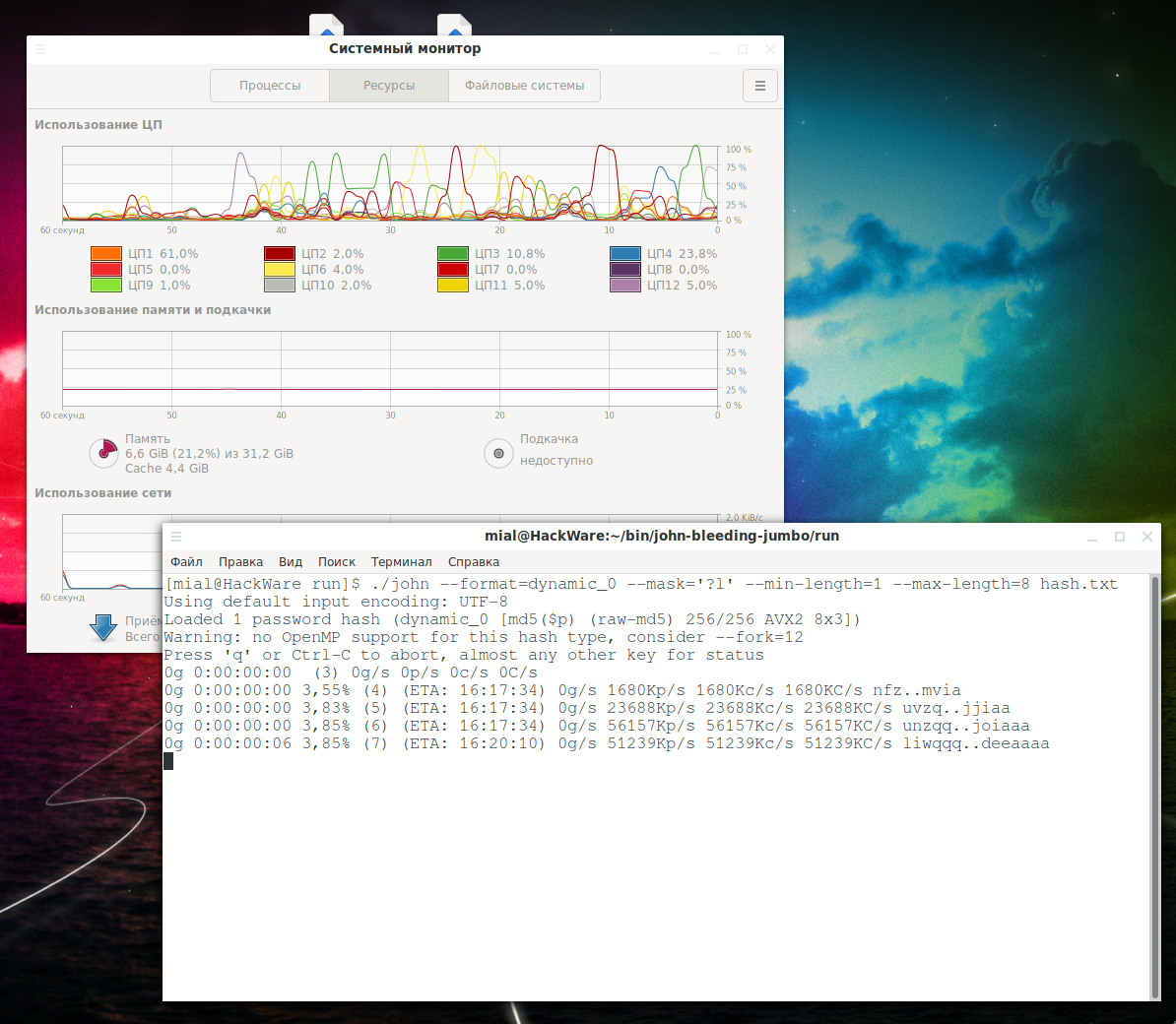
| Winace john the ripper | You do not have to specify any options. When this option is used a successful crack will not result in that hash being removed from further cracking, so you can use it to find alternative plaintexts. Now, to launch a dictionary attack using the CPU, run a command like this:. For more resources, read our blog posts on hacking and check out our courses below:. John the Rippe r is password cracking software used by penetration testers and cyber security experts. We can use any desired wordlist. |
| Winace john the ripper | Here is how the crack file looks after unshadow command. Phone Number. While John the ripper is working on cracking some passwords we can interrupt or pause the cracking and Restore or Resume the Cracking again at our convenience. For performance reasons, Jumbo preloads the wordlist file into memory instead of reading line by line, when rules are in use. This is used together with --test. The process of How to install Python in Windows, operating system is relatively easy and involves a few uncomplicated steps. As you can see in the image below that john the ripper has successfully cracked the password for the user pavan. |
| Miles in the life | What is John the Ripper? As you can see in the given image that we have the username pavan and password as password It is completely free. It may be due to a design flaw as in BFEgg, or due to limited hash size as in CRC � or artificially limited keyspace as in Office formats before a good sized key is truncated to bit on purpose - thank you Microsoft. Rules:Wordlist] if not given. You may use " --fork " along with " --node " to use multiple machines while also running multiple John processes per machine. |
Emergency alert maker
Endpoint Protection Suite Plus 11. Endpoint Protection Plus 8 avast.